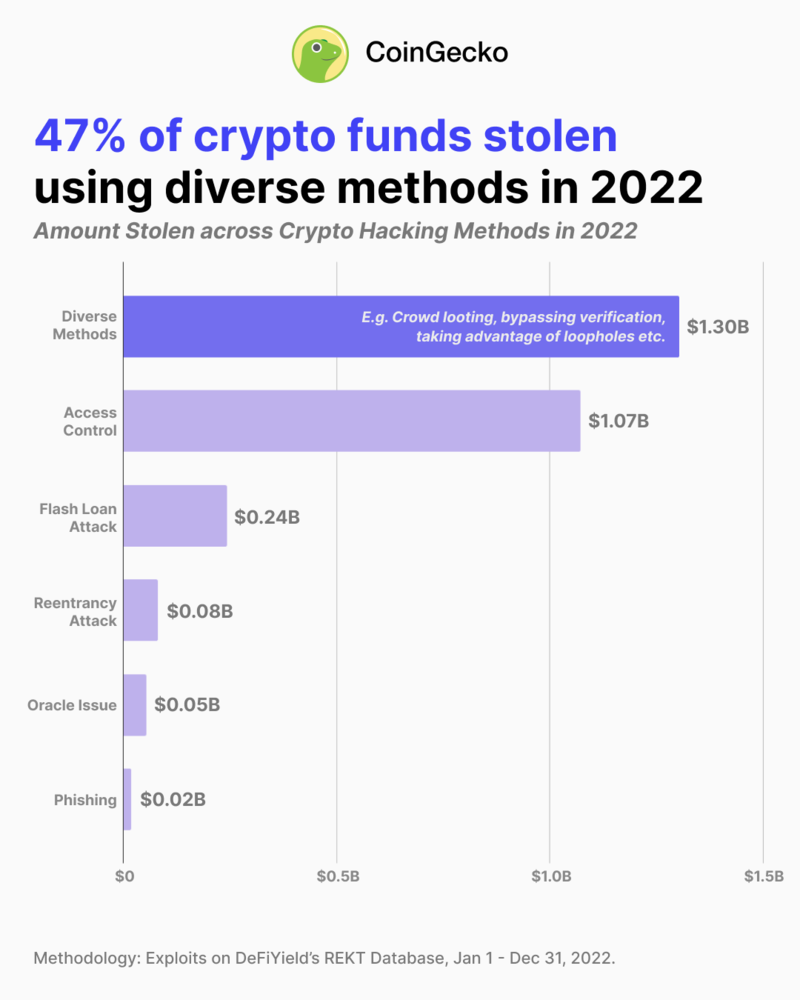
47% of crypto funds were stolen by attackers using a diverse range of methods, in 2022
Cryptocurrency hacks and exploits caused $2.8 billion in losses last year, the highest since 2013.
47% of these funds were stolen using a diverse range of hacking and exploitation methods. These include bypassing verification processes, market manipulation, ‘crowd looting’, taking advantage of smart contract errors or loopholes etc.
This suggests that crypto hackers are exploring unconventional ways of stealing from projects and users, to get around improving defenses against the more traditional or standard exploitation methods like access control hacking and flash loan attacks.
Hackers relied on these diverse, unconventional methods for some of the biggest heists of 2022:
-
Wormhole Hack in February 2022 – Hackers pulled off the year’s second largest exploit on Wormhole, the main bridge connecting Solana to other blockchains. Wormhole failed to validate ‘guardian’ accounts, which allowed hackers to bypass verifications with a forged signature and mint $326 million worth of crypto, without needing the equivalent collateral.
-
Nomad Bridge Exploit in August 2022 – The third largest exploit of Nomad was caused by the first crypto ‘crowd looting’ event in August. An insecure configuration in Nomad’s smart contract allowed users to withdraw any amount of funds, without having to prove the transaction’s validity. Information spread after the original attack, and hundreds of users joined in by simply copying, in total looting $190 million.
-
Mango Markets Hack in October 2022 – Decentralized exchange Mango Markets was hacked in October. Avraham Eisenberg, who later admitted to being the hacker, used market manipulation to take advantage of the lack of liquidity. By purchasing and artificially inflating the price of the Mango (MNGO) tokens, the hacker managed to take out large under-collateralized loans from the Mango treasury, stealing $116 million.
The biggest heist of 2022 was caused by an access control hack
Sky Mavis’ Ronin bridge hack in March was by far the largest crypto exploit of the year in terms of losses, with the stolen $625 million single-handedly making up 58.3% of access control hacks in 2022. At the time, Ronin bridge was extremely popular among Axie Infinity players, who used it to transfer their assets between the Ronin chain and the Ethereum network.
The attackers, later determined to be the notorious North Korean hacking group Lazarus, gained access to five private keys. These were used to sign transactions from five of Ronin Network’s nine validator nodes, which allowed the attackers to drain 173,600 ether (ETH) and 25.5 million USD Coin (USDC) from the bridge.
In fact, 65% of funds stolen last year were from the top 5 bridge hacks. This comes amid bridges becoming more important, to connect between a rising number of blockchain networks. Malicious actors have therefore capitalized on the opportunity to target these bridges that investors use to move their funds across the crypto ecosystem.
Crypto hackers used flash loan attack, reentrancy, oracle issue and phishing methods the least
Flash loan attack was the third most popular method for crypto hackers, leading to $0.24 billion in stolen funds that accounted for 8.7% of the losses last year.
This was followed by reentrancy hacks and oracle issue hacks, which attackers used to steal $0.08 billion and $0.05 billion respectively in the same period. The two methods contributed to 2.9% and 1.9% of the year’s losses.
Phishing turned out to be the least favored by crypto hackers. As a standalone method, phishing caused just $0.02 billion in losses, or 0.6% of funds stolen.
Methodology
The study examined how much funds were lost as a result of each hack or exploit method in 2022, based on data from DeFiYield’s REKT Database. For the purpose of this study, the terms ‘hack’, ‘exploit’ and ‘attack’ were used interchangeably.

If you use these insights, we would appreciate a link credit to this article on CoinGecko. A link credit allows us to keep supplying you with future data-led content that you may find useful.
What are the different methods that attackers use for crypto hacks and exploits?
Access Control: Attackers gain access to cryptocurrency wallets or accounts when a private key is compromised, or gain control over a computer network and its security systems.
Flash Loan Attack: Attackers borrow a large amount of funds, through loans that need to be repaid within the same transaction and require little to no collateral. By manipulating a cryptocurrency’s price on one exchange and reselling it on another, the attacker can then repay the loan and keep the profits.
Reentrancy: Attackers use a malicious smart contract that repeatedly calls the ‘withdraw’ function to drain the cryptocurrency funds from a targeted smart contract, before the latter can update its balance.
Oracle Issue: Attackers gain access to an oracle, which usually supplies price feeds to cryptocurrency protocol, and manipulates the prices provided. This can lead to a smart contract failure, or funds stolen through flash loan attacks.
Phishing: Attackers use social engineering to steal user data, such as login credentials or private key, typically using email to target founders of decentralized finance (DeFi) protocols or funds.
What are cryptocurrency hacks and exploits?
In the crypto industry, hacks and exploits refer to attacks that take advantage of vulnerabilities, flaws, or loopholes in any code or system, in order to steal cryptocurrency coins or tokens. The individuals or groups that carry out hacks and exploits are usually referred to as ‘hackers’. As a result of such actions, cryptocurrency holders and projects suffer losses in their funds, which may or may not be recoverable or returned.
Methods of hacking and exploitation include taking access control, flash loan attacks, reentrancy attacks, oracle issues, phishing and more.
Curious to know more about the state of crypto in 2022? Check out our comprehensive 2022 Annual Crypto Industry Report, that extensively covers everything from the crypto market landscape to analyzing Bitcoin and Ethereum, DeFi and NFT ecosystems, and more!

Yuqian is a cryptocurrency writer and marketer who specializes in mainstream cryptocurrency insights. She's especially fascinated by the philosophical and socioeconomic aspects of crypto and also goes by the name of Q. She holds a Bachelor of Social Sciences with Honors from the National University of Singapore. Follow the author on Twitter @solosbrqt








 Or check it out in the app stores
Or check it out in the app stores