How to Prevent Sandwich Attacks in Crypto?
Traders can safeguard their assets by setting a low maximum slippage, using larger liquidity pools and higher gas, utilizing Telegram bots, and using private RPC networks.
Key Takeaways
-
Sandwich attacks are a type of MEV exploit that deliberately ‘sandwiches’ a transaction by placing orders right before and after the targeted transaction.
-
Attackers exploit the transparent nature of blockchain technology as they are able to scan and view pending transactions on the mempool.
-
Traders can prevent sandwich attacks by setting a low slippage, using larger liquidity pools and higher gas, utilizing Telegram bots, as well as private RPC networks.

What Are Sandwich Attacks in Crypto?
Also known as front-running, a sandwich attack is a type of maximal extractable value (MEV) tactic, where the attacker spots a pending transaction in the network and deliberately ‘sandwiches’ the transaction by placing orders right before and after the targeted transaction. It is also good to note that while front-running is one of the more prominent forms of MEV, there are also other forms of MEV such as back-running, transaction ordering manipulation, and more.
These attacks usually occur on decentralized finance (DeFi) platforms and decentralized exchanges (DEXs) due to their transparency – where transactions are visible on the mempool even before the transaction has been confirmed. This transparency, while a vital feature of blockchain technology, unintentionally allows foul players to scan the blockchain for any large pending transactions to attack.
How Do Sandwich Attacks Work?
An attacker uses a bot to front-run transactions on a blockchain – usually larger transactions. This means that when the victim is making a transaction, the attacker will use the bot to purchase a large buy order just before their transaction goes through, using high gas fees so that their transaction will go through first. As the attacker purchases the token before the victim, this in turn immediately increases the token's price for the victim and the attacker then immediately sells the token at a profit from the victim’s transaction. As the attacker’s sell order is inflated by the transaction, the attacker then profits from the manipulated price difference, often causing the victim to suffer a huge monetary loss.
If you have been in the crypto space for a while, you might have heard of jaredfromsubway.eth – an infamous bot that has profited roughly $34 million in a span of 3 months simply from sandwich attacks. According to Dune, jaredfromsubway.eth has spent more than $90 Million on gas so far and is currently the leading consumer of gas on the Ethereum network, spending more on gas than leading crypto institutions like Binance and Crypto.com.
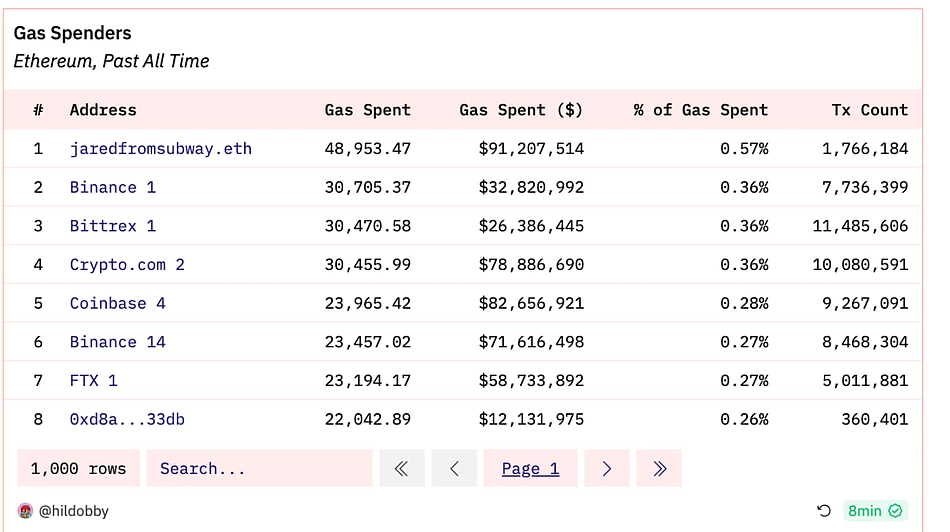
Source: https://dune.com/hildobby/Gas?Timeframe_eab55c=All+Time
As sandwich attacks often occur at the expense of your own holdings, it is important to take note of the various preventive measures you can take to protect your own assets. Sandwich attacks are also not technically illegal yet, which means that the responsibility for safeguarding your assets falls on you.
Now, let’s dive into the steps you can take to protect yourself against sandwich attacks:
Set a Low Slippage
Slippage refers to the difference between the expected shown price of a transaction and the actual price in which the transaction is executed. This change is due to fast-moving markets where the price of an asset can change in a matter of seconds while you are trying to execute your trade. For example, if you set your slippage tolerance to 10%, this means that you are willing to accept the transaction at a price up to 10% higher or lower than the quoted price when you initiated the trade. Otherwise, if the price has fluctuated more or less than 10%, your order will be canceled.
By setting a low slippage, this means that your transaction can only go through if the price of your token remains within a narrow range. Therefore, if an attacker makes a huge purchase before you and the price of the token increases more than your slippage tolerance, your trade will get canceled and not go through. In the case where the attacker purchases just enough tokens to fall within your slippage range – having a low slippage overall still makes the attack much less profitable for the attacker as they will be limited to a much smaller profit margin, safeguarding your tokens.
The usual recommended slippage tolerance of 0.5-1% is usually adequate to accommodate the usual price variations. However, it is good to note that if the slippage is too low, this might result in a failed transaction that can cause wasted gas. You should adjust your slippage tolerance based on a variety of factors such as specific assets, token tax, volatility of the market, and much more.
Use Larger Liquidity Pools
You should also try to use larger liquidity pools when making a transaction. Liquidity pools refer to a collection of funds that are locked in a smart contract which provides the necessary liquidity to facilitate transactions on DEXs. When the liquidity pool is larger, they tend to be less volatile which provides a more stable environment for trading. This also means that they are able to minimize any price fluctuation from individual transactions.
Therefore, to profit off a sandwich attack in a large liquidity pool, an attacker would require significant capital in order to cause the price fluctuations that they benefit from. As such, this can help deter sandwich attackers due to the large capital required for them to manipulate the price.
Pay Higher Gas Fees to Prioritize Transactions
Traders can also opt to use higher gas for their transactions, especially if they are making a larger trade amount which would be more susceptible to sandwich attacks. While using lower gas can save fees, slower transactions allow the attacker to identify and execute the attack.
By using higher gas, the transaction will go through faster and attackers will need to use a much higher gas amount to front-run the transaction. This itself is often costly for the attackers as they would need to use extremely high gas, serving as a deterrent against attacking the transaction. However, as using high gas can often be costly, users should weigh and consider their best option to safeguard their assets.
Utilize Telegram Bots
Telegram crypto bots can directly connect to your wallet and help you to automate and execute a wide range of trades quickly. There are currently a wide variety of bots in the market and while each bot offers differing functions, they generally have the same basic functions like stop loss and take profit orders, anti-rug and honeypot features, copy trading, multi-wallet, liquidity, and method sniping features. Some Telegram bots also offer functions that you can utilize to potentially safeguard you against sandwich attacks.
To counter sandwich attacks, most Telegram bots have a private transaction function which allows users to hide the details of their trade until it is executed. As mentioned earlier, before a transaction is confirmed, the transaction is already visible on the mempool and attackers are able to scan the blockchain for pending transactions to attack. By hiding the details of the transaction under its private function, MEV bots would not be able to view the details of the transaction until it is too late for bots to front-run the transaction.
To name a few, Telegram bots like Unibot, Mizar, and Banana Gun Bot currently offer a private transaction function. Do keep in mind that the bots will also have access to your private keys which can pose a security risk. In October 2023, Unibot experienced an exploit causing the site to lose $630k in funds. While Unibot refunded users who were affected by the exploit, it is a good reminder that while such features are convenient, it is not foolproof and users should always take the necessary precautions to safeguard their assets.
Use a Private RPC Network
A remote procedure call (RPC) node allows applications to communicate with the blockchain network. Most traders currently use public RPC endpoints, which are available for everyone to use. As mentioned above, sandwich attacks occur because the attackers are able to scan and view the pending transaction on the mempool. By using a private RPC network, traders will be able to hide their pending transactions by submitting their transactions straight to the Ethereum network.
Run Your Own Node
To do this, you can choose to run your own node. By setting up your own node, you will be able to submit transactions directly and hide your transactions to prevent attacks. You will also be able to have more control over your transactions such as the timing and processing of your transactions, reducing dependencies on other platforms.
MEVblocker
You can also choose to use MEV Blocker – a free RPC endpoint which helps to protect your trades against MEV. According to the website, MEV blocker does this by sending the trader’s transaction to a network of searchers that scan for back-running opportunities but are unable to front-run your trades. To use the MEV Blocker, users can add MEV Blocker to their wallets such as MetaMask.
Flashbots
Contrary to what its name suggests, Flashbots are not bots. Flashbots is a research and development organization that is focused on researching the MEV space. The organization is dedicated to providing users with a fair platform for trading and combating unfair practices such as frontrunning. The organization currently provides a range of products for users, validators, infrastructure providers and bot operators. Their products currently include Flashbots Protect, Flashbots MEV-Share Node, Flashbots Builders, and more.
For Ethereum traders, users can directly integrate ‘Flashbots Protect’ to their wallets such as MetaMask. This feature not only protects traders from being front-runned by MEV bots, but also offers other features such as preventing users from their transaction reverting. The Flashbots Protect feature connects users to a private RPC network, allowing them to transmit their transactions directly to miners without exposing them to the public mempool where they are susceptible to MEV attacks.
Final Thoughts
Unintentionally, sandwich attacks exploit the transparent nature of blockchain technology which was meant to uphold a standard of openness and trust among the community. As cryptocurrency remains less regulated as compared to other financial markets, it presents a unique set of challenges that investors have to face. As crypto continues to progress and advance, I am sure that we will witness other forms of attacks. As such, traders and investors need to be aware of the potential risks of unfair trading practices so that they will be able to better safeguard their assets.

Hwee Yan has been involved in the cryptocurrency space since 2021. Currently pursuing a degree in Linguistics and Multilingual studies at Nanyang Technological University, she is a writer who is mainly interested in NFTs, crypto trends and memecoins. Follow the author on Twitter @cryptohy8




 Or check it out in the app stores
Or check it out in the app stores
